PHP v8.1.28 released
The PHP security release 8.1.28 was launched on April 11, 2024. These were Eid-ul-Fitr holidays in Pakistan.
The first CVE that I have reviewed is Critical. However, it does not impact our line of work much, because:
- We do not use the Windows web servers. Linux is our server of choice.
- The vulnerability relates to the proc_open() command executions and at high level, we usually never use this function. Thus, the implicit spawning of cmd command using CreateProcess will not impact us. [Looking at it at a very high level and not digging deep into the framework source code either]
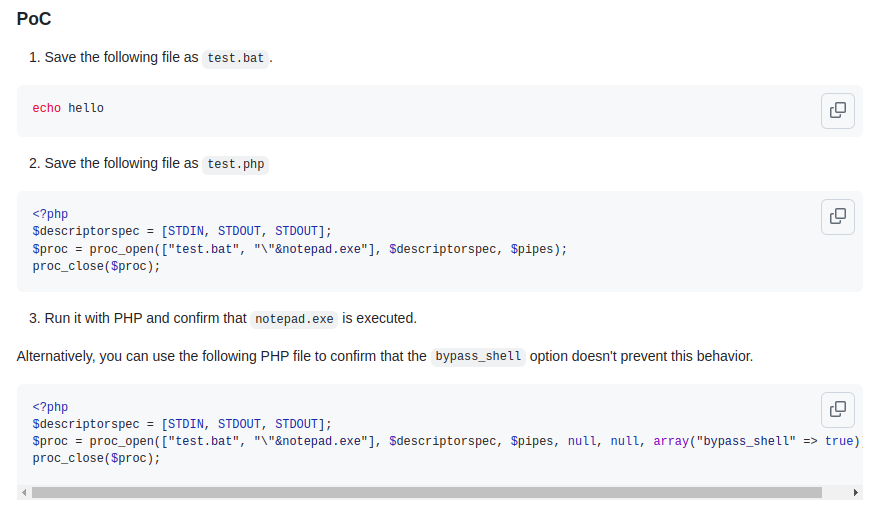
This Github advisory is a proof of concept of the implications of this vulnerability:
https://github.com/php/php-src/security/advisories/GHSA-pc52-254m-w9w7
The second CVE reported is related to the Account Takeover (ATO) risk. Although the scenario does not seem to work for the most of the online accounts out there, but it is still a possibility. The following conditions should fulfill as a precursor to this attack:
- User should have the account password saved and it should start with a Null byte (\x00).
- The server should be verifying the passwords with password_verify() PHP function.
- The attacker should be able to bypass the frontend password validation.
- The attacker should be able to bypass the server side input validation.
If all of the above conditions are met and the attacker is able to send an empty string as password the server, the password_verify() function will return TRUE. Voila!
I shall review the remaining vulnerabilities later and update here.